Homebrew (video games)
hideThis article has multiple issues. Please help or discuss these issues on the talk page. (Learn how and when to remove these template messages)
|
Homebrew, when applied to video games, refers to games produced by hobbyists for proprietary hardware platforms that are not intended to be user-programmable, primarily video game consoles. These often use storage formats that make distribution difficult (such as ROM cartridges or encrypted CD-ROMs). Many systems have hardware restrictions to prevent unauthorized development. A non-professional developer for a system intended to be user-programmable, like the Commodore 64, is simply called a hobbyist (rather than a homebrew developer).
Homebrew development can include software made using unofficial, community maintained toolchains or games developed using official development kits such as Net Yaroze, Linux for PlayStation 2, or Microsoft XNA.[1] Some targets for homebrew games include the Wii, Dreamcast, Game Boy Advance, PlayStation Portable, Nintendo Entertainment System, and Atari 2600.
Development[]
New games for older systems are typically developed using emulators. Development for newer systems usually involves actual hardware, given the lack of accurate emulators. Efforts have been made to use actual console hardware for many older systems, though. Atari 2600 programmers may burn an EEPROM to plug into a custom cartridge board or use audio transfer via the Starpath Supercharger. Game Boy Advance developers have several ways to use GBA flash cartridges in this regard.
Second generation consoles[]

Atari 2600[]
Odyssey[]
In 2009, Odball became the first game for the Magnavox Odyssey since 1973. It was produced by Robert Vinciguerra[2] who has since written several other Odyssey games. On July 11, 2011, Dodgeball was published by Chris Read.[3]
Channel F[]
A handful of games have been programmed for the Fairchild Channel F, the first console to use ROM cartridges. The first known release is Sean Riddle's clone of Lights Out which included instructions on how to modify the SABA#20 Chess game into a Multi-Cartridge.[4] There is also a version of Tetris and in 2008 "Videocart 27: Pac-Man" became the first full production game for the system since it was discontinued.
Third and fourth generation consoles[]
NES[]
Several compilers are available for the Nintendo Entertainment System, but like the Atari 2600, most development directly applies assembly language. One impediment to NES homebrew development is the relative difficulty involved with producing physical cartridges, although third-party flash carts do exist, making homebrew possible on original NES hardware.[5] Several varieties of custom processors are used within NES cartridges to expand system capabilities; most are difficult to replicate except by scavenging old cartridges. The hardware lockout mechanism of the NES further complicates the construction of usable physical cartridges. However, the NES-101 removed the 10NES lockout chip so any game, whether homebrew, unlicensed, or another region of an official game, can be played. The original Famicom and its clones also feature no lockout mechanism. The 10NES chip can eventually be permanently disabled by performing a minor change to the hardware.
Genesis[]
The Sega Genesis has no physical lockout mechanism, making it easier to release software for the system. Rick Dangerous, Rick Dangerous 2, Pier Solar and the Great Architects, and a port of Teenage Queen were released as physical cartridges. Other games include Sacred Line Genesis, Coffee Crisis, and Frog Feast for the Genesis and Mighty Mighty Missile for the Sega Mega-CD. The 2018 game Tanglewood was developed using original Sega development hardware.[6]
TurboGrafx-16/PC Engine[]
This section does not cite any sources. (May 2018) |
The TurboGrafx-16/PC Engine has a comparatively small homebrew scene. The first homebrew title released on CD was 's Implode in 2002, a few years after the system's last official release (Dead Of The Brain I & II for the PC Engine in 1999). Two years later, MindRec released Meteor Blaster DX on CD-R. Official word was that it was unable to be pressed to CD proper due to the glass mastering software suddenly unable to handle the unorthodox style of CD layout that the system expects. Five years later, Aetherbyte Studios released Insanity, a Berzerk clone, on pressed CD, quelling the notion of unpressable CDs. Aetherbyte later went on to prototype and produce a new HuCard design called "AbCARD", which was fully compatible with the console.
There is one C compiler for the console known as HuC. It has not been officially updated since 2005. The MagicKit assembler is generally considered[by whom?] the de facto assembler for the console, and comes included with HuC. Additional libraries for HuC/MagicKit include Squirrel, a sound engine developed by Aetherbyte Studios, and the SGX/ACD library, developed by Tomatheous, that gives the developer easy access to the SuperGrafx video hardware as well as the Arcade Card.
The cc65 C compiler is compatible with the console, although there is no development library support for it.
SNES[]
This section does not cite any sources. (May 2018) |
Bung Enterprises released the Game Doctor SF hardware series. It allows users to copy games and run new games on SNES hardware. ROMs can be converted into the Game Doctor SF format and put onto a 3 1/2" floppy. Games as large as twelve megabits can be put on floppy disks formatted to 1.6 megabytes.
An alternative device is the Super Flash, by Tototek, which allows multiple games to be burned onto a flash memory chip in a cartridge. This allows games as large as 48 megabits.
The run and gun game, Alisha’s Adventure, used original Super Famicom development hardware.[7]
Neo-Geo MVS, AES, and CD[]
The Neo-Geo Home Cart and Arcade Systems can be tough candidates for homebrew development. Neo-Geo AES and MVS cartridges have two separate boards: one for video, and one for sound. If programming a cartridge for the system were to occur, it would involve replacing the old ROM chips with one's newly programmed ones as the cartridges are in a sense, Arcade boards. NGDevTeam who have released Fast Striker and Gunlord found a workaround with this. What they did was print out their own board, and soldered their own ROM chips into them; this, however, can cause the Universe Bios logo to look corrupted if a custom bios were to be programmed. Programming for the Neo-Geo CD, however is easier than programming for cartridges. The CDs themselves can actually contain both sound and video respectively. Depending on the Megabit count for a game program, load times will vary. A CD game with low Megabit counts will load only one time; whereas a CD game with higher megabit counts could load in between scenes, or rounds. There are now some full games scheduled[when?] for release in physical form, such as Neo Xyx.[citation needed][8]
Programmer of the Neo-Geo Universe Bios, Razoola is currently[when?] working on a "Skeleton Game Driver" that supports two players. This ROM is meant to remedy the corrupted Universe Bios Screens, as well as work with an unmodified/stock Neo-Geo Multi-Video System (MVS), or Advanced Entertainment System (AES).[9]
Fifth generation consoles[]
Jaguar[]

The Atari Jaguar has its own dedicated homebrew community. Its first hobbyist-developed game was released in 1995: a version of Tetris called JSTetris written using a hacked version of the Alpine Development Kit, one of the pieces of hardware used to program official Jaguar games.[10] After purchasing all the intellectual property assets of Atari Corporation from JTS in 1998,[11] Hasbro Interactive, on May 14, 1999, announced that they have released all rights to the Jaguar, declaring the console an open platform.[12][13] Following the announcement, a few developers and publishers, such as AtariAge, B&C Computervisions, Piko Interactive, Songbird Productions, Telegames, and Video61, have released both previously unfinished games from the Jaguar's past as well as several brand new games.[14]
Since emulation of the console is still limited, coding uses a real console through either the Skunkboard development cartridge, using a BJL modified Jaguar, or the official Alpine Development Kit. The commercial game BattleSphere Gold, also contains the JUGS (Jaguar Unmodified Game Server) aid to development.[15]
Games are released in either cartridge, CD–or both–formats. Most developers have published their works either online on forums or in cartridge via independent publishers. Since both systems do not have regional locking, all of the titles are region free. Some of the earliest CD releases were not encrypted, requiring either B&C's Jaguar CD Bypass Cartridge[16] or Reboot's Jagtopia (Freeboot) program burned into a CD in order to run unencrypted CD games,[17] but Curt Vendel of Atari Museum released the binaries and encryption keys for both the cartridge and CD format, making it possible to run games without the need of development hardware.[18] A cracked BIOS of the Jaguar CD can be soldered inside the system.[19]
There are also ST-to-Jaguar conversions, which involves porting titles from the Atari ST to the Jaguar, which may include some enhancements.[20] While they can be downloaded for free, select titles were sold on August 3, 2016[21][22][23] and others, as of date, are being licensed and sold in festivals dedicated to the system such as E-JagFest, JagFest or online via AtariAge.[24]
PlayStation[]
Making games on the PlayStation is possible with any model of the system through the use of a modchip or the double 'Swap Trick'. Requirements consist of a PC, SDK, and a 'Comms Link' device to upload and download files to and from the console.
Another way of starting homebrew on the PlayStation is 'UniROM', which is a Softmod. UniROM works by being installed onto a cheat-device, which is connected via the parallel-port (on old consoles) and allows loading of custom code via burned CDs and the serial port.
Homebrew was originally promoted by Sony with the Net Yaroze, which had a large scene for quite some time. However, the official Net Yaroze site was shut down in mid-2009, and Sony stopped supporting the system as well as the users who still owned the console.
Saturn[]
The Sega Saturn homebrew scene is small but active. As with the PlayStation, all models are capable of homebrew. Modchips for the Saturn Model 1 have been scarce for some time, as it seems that no one has produced any new modchips in years. As such, the only two options left are to either perform the swap trick or extensively modify a Saturn Model 2 modchip.
Running homebrew on the Model 2 can be accomplished by bridging two points on the modchip, soldering a wire from the modchip to the Saturn power supply, and inserting it where the CD-rom ribbon cable inserts. The swap trick is more difficult to pull off on this Model due to the lack of an access light.
Another method is what is known as the "PseudoSaturn" unlocking method. It is a program created by CyberWarrior2000 that abuses the "Pro Action Replay" cartridge's firmware. It unlocks region, frequency, and CD protection of most Saturn models. Either a modded Saturn or a swap trick is required to run the installer, which loads the code in the FlashROM of the cartridge. Afterwards, the cartridge unlocks everything and most software can be run, from backups to homebrews. There is also now a new engine for development called the Jo-Engine created by Johannes Fetz to allow easy development of 2D games.[25] This engine is currently able to compile 2D games without the Sega Graphic Libraries (SGL). Another engine by XL2, called the Z-Treme engine, led to the creation of a fully 3D Sonic The Hedgehog game called Sonic Z-Treme.[26] Z-Treme uses Sega Basic Libraries (SBL) and Sega Graphic Libraries (SGL).
Virtual Boy[]
Planet Virtual Boy has promoted homebrew for years by the site, since the system has no region lock.[27] But it wasn't until the flash carts FlashBoy and FlashBoy+ were released that the homebrew scene began to grow. Despite the Virtual Boy's mere 8 months in production before being discontinued (August 1995 - March 1996), dedicated fans have been making a variety of homebrew games for years. Two previously unreleased games, Bound High! and Niko-Chan Battle (the Japanese version of Faceball) have been released.
Nintendo 64[]
The Nintendo 64 homebrew scene is small, but homebrew can still be played and developed through the use of a Doctor V64, (Acclaim used a Doctor V64 to help develop Turok,[28]) the Everdrive 64[29] or 64drive.[30]
Sixth generation consoles[]
Dreamcast[]
Despite its short commercial lifespan of less than two years in North America, the Dreamcast benefits from an active homebrew scene even ten years after its discontinuation. Due to a flaw in the Dreamcast BIOS, which was intended for use with MIL-CD's, the console can run software from CD-R without the use of a modchip. Sega reacted by removing MIL-CD support from the BIOS of the later produced Dreamcast consoles manufactured from November 2000 onwards.
The console is especially notable for its commercial homebrew scene. One notable project was the Bleemcast! emulator, which was a series of bootdisks made to play PlayStation games on the system, featuring visual enhancements over the original console. Newer independent releases include Last Hope, released by RedSpotGames in 2007, and DUX,[31] both Shoot 'em up style games. These releases were written using the KallistiOS development system. A port of the freeware high-level development language Fenix and BennuGD is available for use in game development; many DIV Games Studio games have been ported and others were originally written for the system.
PlayStation 2[]
Early versions of the PlayStation 2 have a buffer overflow bug in the part of the BIOS that handles PS1 game compatibility; hackers found a way to turn this into a loophole called the PS2 Independence Exploit, allowing the use of homebrew software. Another option for homebrew development is the use of a modchip. Also, it is possible for developers to utilize a PS2 hard drive and HD Loader. In Europe and Australia, the PS2 came with a free Yabasic interpreter on the bundled demo disc for some time. This allows simple programs to be created for the PS2 by the end-user. This was included in a failed attempt to circumvent a UK tax by defining the console as a "computer" if it contained certain software.[32] A port of the NetBSD project and BlackRhino GNU/Linux, an alternative Debian-based distribution, are also available for the PS2.
Using homebrew programs (e.g. 'SMS Media Player'[33]) it is possible to listen to various audio file formats (MP3, OMA, Ogg Vorbis, AAC, FLAC, AC3), and watch various video formats (DivX/XviD, MPEG1, MPEG2, MPEG4-ASP in AVI Container) using the console. Media can be played from any device connected to the console i.e. external USB/FireWire/thumb drive/hard disk drive (FAT32 only), the internal hard disk on early revision consoles, optical CD-R(W)/DVD±R(W) disks (modded systems or patched disks), or network shares (Windows Network or PS2 host: protocol).
A more recent development (May 2008) called Free McBoot allows homebrew programs to be launched without a trigger disc required by the older exploit. This also allows use of homebrew on unmodded systems without a functional disc drive. However, installation of the exploit to each individual memory card requires either an already exploited/modded system in order to launch the installer, or boot image that can load an app that loads ELF files (network adapter and hard drive also required). Copying from one memory card to another will not work. This newer exploit will not work on the very newest PS2s (SCPH-9000x model with BIOS 2.30 and up) but will work on all models prior to that. The newest versions of Free McBoot, version 1.90 and newer, also have the ability to install and boot from both Sony and non-Sony HDDs when using a "fat" PS2 and network adapter.[34] This support is called Free HDBoot or FHDB. With a few minor issues, it is now possible to game entirely from the HDD, without needing to use the optical disc drive nor a physical memory card.
Unlike the Independence Exploit, which requires a trigger disk, Free McBoot needs only a standard Memory Card, which allows it to be used on systems with broken optical drives. The installation is keyed to the Memory Card and will be usable on only the same version consoles that it was originally installed on, unless a Multi-Install is performed. The drawback of this exploit is that it needs to be installed/compiled on each individual memory card. Simply copying the exploit is not possible; this means that an already modded or exploited system is required to install FMCB on a Memory Card. After installing an exploit, unsigned executables (Executable and Linkable Format) may be launched from a Memory Card or a USB drive. Such programs include emulators, media players, hard drive management tools, and PC-based or NAS-based file shares. The exploit is also notable for allowing the user to copy PS1/PS2 save files from a Memory Card to a USB drive, a functionality normally only possible with tools such as a DexDrive.
Sony released a Linux-based operating system for the PS2 in a package that also includes a keyboard, mouse, Ethernet adapter and HDD. Currently, Sony's online store states that the Linux kit is no longer for sale in North America. However, as of July 2005, the European version was still available. The kit boots by installing a proprietary interface, the run-time environment, which is on a region-coded DVD, so the European and North America kits only work with a PS2 from their respective regions.
Homebrew emulators of older computer and gaming systems have been developed for the PS2.[35]
GameCube[]
Homebrew development on the Nintendo GameCube tended to be difficult, since it uses a proprietary MiniDVD-based drive and media as opposed to the standard DVD drives of the PS2 and Xbox for piracy protection. Also, its connectivity is limited, as it does not feature a USB port or an HDD port like the PlayStation 2.
The barrier to burning Nintendo GameCube discs with a consumer DVD burner is the Burst Cutting Area, a "barcode" in the innermost ring of the disc, an area inaccessible to most burners and writeable only by very expensive disc pressing machines. For a long time the only way to run homebrew software on Nintendo GameCube was through a patching-system exploit of Phantasy Star Online Episode I & II, requiring users to find the game and a Broadband Adapter. Both of these are difficult to find because a follow-up has been released (under the name Phantasy Star Online Episode I & II Plus) and thus the original PSO was rarely sold after then, and because the Broadband Adapter was not often carried in stores due to the Nintendo GameCube's very limited selection of online games.
As of August 2019, the most common method is to use an Action Replay in conjunction with an SD card adapter inserted into the memory card slot, allowing the user to run homebrew from the SD card, or over Ethernet. Another method involves using a modchip to allow the GameCube to run homebrew from a MiniDVD-R via the disc drive. Another method uses a save game exploit which involves transferring modified game save files to a GameCube memory card that triggers arbitrary code execution when loaded by an official game, allowing custom software to be run from a memory card, SD card, or other media.[36] As the Nintendo GameCube's case does not fit a full-size DVD-R, third party replacement cases are available.
Homebrew software for the Nintendo GameCube mainly consists of emulators for other systems, as well as several popular homebrew utilities. Swiss is an “all-in-one homebrew utility”, including a file browser, and the ability to force software to use different video modes that aren't officially supported, such as progressive scan or 16:9 widescreen.[37] The Game Boy Interface is a homebrew software frontend for the Game Boy Player peripheral, and is often used for capturing high-quality footage from Game Boy, Game Boy Color, and Game Boy Advance games.[38]
Xbox[]

The Xbox console uses several measures, including cryptographically signed code to obfuscate firmware. The primary method of executing homebrew code required installing a mod chip which could be flashed with a modified Microsoft BIOS. This BIOS allowed the system to boot unsigned executables (XBEs) and control several hardware variables, such as region coding and video mode. With the leak of Microsoft's official development kit (XDK), homebrew coders were able to write replacement Xbox GUIs (known as dashboards), games and applications for the Xbox.
A softmod, which uses a commercial game such as 007: Agent Under Fire, Mech Assault, or Splinter Cell, had been created to execute a persistent softmod installer without modification of the hardware. This method utilizes modified font and sound files to cause the Xbox to cause a stack buffer overflow and load a homebrew dashboard. Once in this condition, the Xbox is able to execute homebrew games and applications upon boot up.
Due to the Xbox using standard PC libraries, writing homebrew games is relatively easy and the vast majority of libraries available for a PC programmer are available to an Xbox homebrew programmer.
One of the more common type of homebrew games for the Xbox are ports of PC games whose source has been publicly released or leaked. Many classic PC games have been released for Xbox, but most are created with the XDK which limits their availability. The only places to find these ports are through IRC or peer-to-peer browsers.
The Xbox system is also very adept at running emulators which have been ported from PC, given its high processing power. The Xbox is able to emulate systems up to the previous generation, including the Nintendo 64 and the PlayStation. For this reason, many different emulators have been created for or ported to the Xbox.
Game Boy Advance[]
The popularity of homebrew development for the Game Boy Advance system since its release in 2001 is due to the availability of C compilers and ready-made, high-quality code libraries, and debugging features for Game Boy Advance emulators like the VisualBoyAdvance-M, the mgba, the No$gba GBA Emulator, John GBA and My Boy. Also contributing to the success is both the nostalgia for the system in general, the Pokémon Romhacking community, and the wide availability of Flash ROM cartridges and cartridge writers in online shops.
Seventh generation consoles[]
PlayStation Portable[]
Nintendo DS[]

Since the release of the Nintendo DS, a great deal of hacking has occurred involving the DS's fully rewritable firmware, Wi-Fi connection, game cards that allow SD storage, and software use.[citation needed] There are now many emulators for the DS, as well as the NES, SNES, Sega Master System, Sega Mega Drive, Neo-Geo Pocket, Neo-Geo MVS (arcade), and older handheld consoles like the Game Boy Color.[39]
There are a number of cards which either have built-in flash memory, or a slot which can accept an SD, or MicroSD (like the DSTT, R4, AceKard and ez-flash V/Vi) cards. These cards typically enable DS console gamers to use their console to play MP3s and videos, and other non-gaming functions traditionally reserved for separate devices.[40]
In South Korea, many video game consumers exploit illegal copies of video games, including for the Nintendo DS. In 2007, 500,000 copies of DS games were sold, while the sales of the DS hardware units was 800,000.[41]
Another modification device called Action Replay, manufactured by the company Datel, is a device which allows the user to input cheat codes that allows it to hack games, granting the player infinite health, power-ups, access to any part of the game, infinite in game currency, the ability to walk through walls, and various other abilities depending on the game and code used.[42]
Photographer Steve Chapman, looking for other ways to continue his photography work with smaller equipment, created DS-DSLR, an application that allowed him to control his camera without his bulky laptop. When his camera was connected to the DS through the GBA cartridge slot, DS-DSLR allowed him to execute many tasks, including controlled bracketing, custom interval shots, and timed long exposures. DS-DSLR even had a noise-activated shutter control which was activated when the DS mic detected noise.[43]
With the DSi, it too has some homebrew exploits, some of which use DSiWare apps such as Flipnote (aka ugopwn), sudokuhax, using a game called Sudoku by EA Games, grtpwn, exidiahax, fieldrunhax, 4swordhax, UNO*hax, and a exploit using Petit Computer called petit-compwner. There is also systemflaaw, which uses the DSi-exclusive game System Flaw,
A user by the name of shutterbug2000 on GBAtemp has released 2 DSi exploits, one being called Memory Pit, an exploit using the DSi Camera app,[44] and the Flipnote Lenny exploit (aka ugopwn), using Flipnote Studio.
Xbox 360[]
Microsoft has released a version of its proprietary Software Development Kit (SDK) for free, to would-be homebrew programmers. This SDK, called XNA Game Studio, is a free version of the SDK available to professional development companies and college students. However, to create Xbox 360 games one must pay for a premium membership to the XNA Creators Club. Once the games are verified, the games written with XNA Studio can be made available for 80, 240, or 400 Microsoft Points to all Xbox 360 owners (through Xbox Live). This allows creators of homebrew content access to their target audience of Xbox 360 owners. This content is available under the Indie Games section of the New Xbox Experience.
On March 20, 2007, it was announced that a hack using the previously discovered hypervisor vulnerability in the Xbox 360 kernel versions 4532 and 4548 had been developed to allow users to run XeLL, a Linux bootloader. The initial hack was beyond the average user and required an Xbox serial cable to be installed and a flashed DVD Drive firmware. Felix Domke, the programmer behind XeLL, has since announced a live bootable Linux CD suitable for novice users, with the capabilities to be installed to the SATA hard drive of the Xbox 360. Despite the availability of such a distribution, the Xbox 360 still isn't considered a popular platform for homebrew development, given the dependence of the exploit on the DVD-ROM being able to load a burnt DVD game, a modified version of the game King Kong, and two older kernel revisions of the console itself.
A group independent of Microsoft is working on the means to run homebrew code, as part of the Free60 project.
Note: The hypervisor vulnerability in the Xbox 360 kernel versions 4532 and 4548 was addressed by Microsoft with the release of the NXE system and dashboard update in 2008.[citation needed]
Homebrew was since re-enabled on any Xbox 360 with dash 2.0.7371.0 or lower via an exploit referred to as the jtag / jtag smc hack but was promptly patched again by Microsoft with the 2.0.8495.0 update.
Homebrew has now become available on most if not all Xbox 360 consoles due to the Reset Glitch Hack. So far it works on all current dashboards up to as of now the latest 17526 dashboard. Although it can run unsigned code some hardware is required to do the hack/exploit. Also soldering skills are a necessity when attempting to use this exploit.
PlayStation 3[]
The PlayStation 3 was designed to run other operating systems from day one. Very soon after launch, the first users managed to install Fedora Core 5 onto the PlayStation 3 via the 'Install Other OS' option in the PlayStation 3's XMB (Xross Media Bar), which also allows configuring the PlayStation 3 to boot into the other OS installed by default.
So far, several Linux flavors have been successfully installed to the PlayStation 3, such as Fedora Core 5, Fedora Core 6, Gentoo, Ubuntu and Yellow Dog Linux (YDL). The latter comes installed with the Cell SDK by default, allowing programmers a low cost entry into Cell programming. See also: Linux for PlayStation 3
Originally, graphics support was limited to framebuffer access only (no access to the PlayStation 3's graphics chip RSX), yet some access to the RSX graphics processor was achieved (but Sony blocked this with firmware release 2.10).
As of firmware release 3.21, consumers are no longer able to access the 'Other OS' due to Sony removing the facility[45] from the software in an update. Sony said this was in response to several 'security concerns'.
Homebrew developers do have access to the Cell microprocessor, including 6 of its 7 active Synergistic Processing Elements (SPEs). The Game OS resides under a hypervisor and prevents users from taking full control of the PlayStation 3's hardware. This is a security measure which helps Sony feel secure enough to allow users to install other operating systems on the PS3.
The Sixaxis controller has also been exposed to Linux and Windows,[46] but no driver seems to have been successfully created yet that exposes its accelerometer functionality, except for Motioninjoy. However other drivers have successfully used it as a controller for gaming and other applications.
In May 2008, a vulnerability was found in the PlayStation 3 allowing users to install a partial debug firmware on a regular console. However, the debug functionality is disabled, so neither homebrew applications nor backup games can be run yet.
Another exploit was found on August 14, 2008, allowing users to boot some backup games from the PlayStation 3's HDD, although the exact instructions on how to do this were not released at that time. However, a different person posted instructions 10 days later, which explained the exploit.[47]
On January 6, 2009 a hacking ring known as the "Sh4d0ws" leaked the jig files needed to launch the PlayStation 3 into service mode. Although the PlayStation 3 can be triggered into service mode, it is not yet of any use because the files needed to make changes to the console have not been leaked.[48]
On August 31, 2010, PSGroove, an exploit for the PS3 through the USB port, was released and made open source. This exploit works on all of the PS3 models released up until then.[49] A guide for the creation of the PSGroove is available through several online sources.[50]
George Hotz, better known under his nickname "geohot", has recently appeared on Attack of the Show because he released the PlayStation 3's encryption keys, therefore any Homebrew or custom firmware can be signed. Once signed, homebrew can be natively run. It would be difficult for Sony to fix this because it would most likely require a voluntary recall and the most expensive parts would have to be replaced.[51] In 2011, Sony, with help from law firm Kilpatrick Stockton, sued Hotz and associates of the group fail0verflow for their jailbreaking activities. Charges included violating the DMCA, CFAA, Copyright law, and California's CCDAFA, and for Breach of Contract (related to the PlayStation Network User Agreement), Tortious interference, Misappropriation, and Trespass.[52]
Wii[]

In advance of the Wii's release, WiiCade was the first site to host Adobe Flash homebrew games specifically designed for the Wii and its remote, which could be played without any exploits using the Wii's Opera web browser.[53] The Wii was hacked via a custom serial interface in December 2007.[54] The goal of most Wii exploits is to install The Homebrew Channel, a custom channel that lets users run homebrew software on the console. The Homebrew Channel's first full release was in December 2008.[55] Though Nintendo successfully patched various older exploits to install The Homebrew Channel, many exploits to run the channel on current firmware exist. This channel can be installed using exploits in games such as Super Smash Bros. Brawl, an exploit in the Internet Channel,[56] a DNS exploit with the EULA, or it can be installed via an exploit in the Wii's messaging system.[57] Note that only exploits that use disc games are compatible with installing The Homebrew Channel on the vWii (virtual Wii) mode on a Wii U, with the exception of "wuphax", an exploit that installs the channel via Wii U specific system permission exploits. The Wii Opera software development kit let developers make their own games in JavaScript.[58] The console's controller was also a popular target for modification.[59] On Aug 9, 2010, Team Twiizers released an exploit called LetterBomb which uses a malformed mail letter (Buffer overflow) to load a boot.elf file into memory, which then installs The Homebrew Channel to run unsigned code.
In recent years, other methods exploiting the Internet Channel (Flashhax), the Wii's EULA (str2hax[60]), and the Wii Message Board (letterbomb) have been released. In 2019, an exploit using Bluetooth called bluebomb[61] was released. Bluebomb meant that the Wii Mini was hackable for the first time, as it was previously not possible due to the Wii Mini's Internet and Wii messaging capabilities, and SD slot removed.
Eighth generation consoles[]
3DS[]
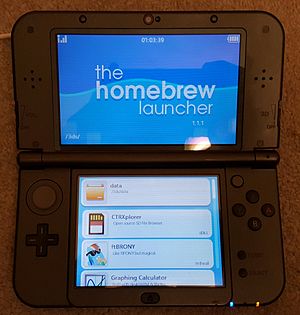
The first public homebrew exploit for the Nintendo 3DS, ninjhax, allowed the user to scan a QR Code to exploit the game Cubic Ninja. Other ways to run The Homebrew Launcher have been discovered since then, including freakyhax, an exploit in the Deluxe edition of Freakyforms: Your Creations, Alive!,[62] Doodlebomb, an exploit in the 1.1.1 and older versions of Swapdoodle,[63] and smashbroshax, a New 3DS exclusive exploit for the 3DS version of Super Smash Bros. for Nintendo 3DS and Wii U.[64]
The majority of system updates that have "Further improvements to overall system stability and other minor adjustments have been made to enhance the user experience" in their changelog are simply to patch Homebrew Launcher (userland) exploits that require a specific version of a game or application are often patched in these updates by adding those exploited application versions to the "IsTitleAllowed" blacklist, which prevents outdated applications on the list from launching, forcing users to update those applications to the latest version to launch the application.[65] For example, notehax only works on outdated versions of Flipnote Studio 3D. In the 11.6.0-39 system update, all regions of Flipnote Studio version <=1.0.1 in USA, <=1.2.0 in EUR, and <=1.3.1 in JPN were blocked from launching the application, patching the exploit on current firmware.[66][67]
Unsigned software can be launched from the SD card without having to install custom firmware on the device by using an exploit to run The Homebrew Launcher. The Homebrew Launcher itself can be launched on system versions 9.0-11.13 on any 3DS system. However, without installing custom firmware, the user will need to run the exploit each time they want to access The Homebrew Launcher.
To directly install custom software onto the 3DS home menu, a custom firmware is needed. There are several custom firmware releases available, the most popular being Luma3DS. Requirements to install custom firmware involve using various exploits to run a bootrom exploit called boot9strap, which executes custom code before boot ROM lockout. As of December 2020, the latest exploit uses an oversight in DSiWare, which can run the custom code from the DSiWare menu in the 3DS settings to install the 3DS hacks.[68]
Vita[]
In 2016, an exploit for the PlayStation Vita was released named "HENkaku".[69] This exploit used a bug found on the 3.60 system firmware, allowing users to run unsigned software. It was installed by visiting a website and clicking on the install button on the PlayStation Vita web browser. This had to be done every time the user turned the system on. In the 3.61 system update, Sony patched the bug to make it impossible to run unsigned code on the Vita. However, in 2018, computer science student TheFloW (Andy Nguyen) found a kernel bug in firmware versions 3.65, 3.67, and 3.68 that allowed unsigned code to be run. Eventually, he developed an exploit called "h-encore" which allowed one to install the HENkaku hack on later PS Vita versions. The kernel bug was patched in firmware version 3.69, but the userland bug still works. Because HENkaku needs to be reinstalled everytime the device is turned on again, an optional flasher program named ensō can be used alongside HENkaku to flash it into the system, making the plugin stay permanently even after shutdown and reboot, until uninstalled through the ensō installer.
On February 13, 2019, TheFloW released a downgrader tool that can downgrade any Vita console to an older firmware down to its factory firmware.[70]
Wii U[]
This section may contain an excessive amount of intricate detail that may interest only a particular audience. (May 2017) |
The Wii U currently has homebrew execution in both the PowerPC kernel and the ARM9 kernel (nicknamed IOSU by the community). The most common way to execute code on the Wii U for 5.5.1 and below is through vulnerabilities in the Wii U's built in web browser. There are many different userland and PowerPC kernel exploits in the Wii U internet browser. The earliest userland exploits used C code (on versions 2.0.0-5.3.2) and libstagefright bugs (on versions 5.4.0-5.5.1) to load custom code in the browser, with memory and permission limitations.[71][72] The first kernel exploit found in the browser, called osdriver, only works on system versions 5.3.2 and lower, but this is no longer used as the 5.5.1 and lower exploit is more reliable. Currently, two different browser kernel exploits are used in the community. The first exploit found works on 5.5.1 and below and is very reliable.[73] The other kernel exploit works on 5.5.2 and below, but due to its unreliability, it is only used on 5.5.2 to install a Wii U software exploit called Haxchi. Haxchi exploits the fact that DS Virtual Console game data is only checked when the game is installed. When installed to a DS VC game, Haxchi launches homebrew directly (such as the Wii U Homebrew Launcher) using an exploit installed in the game's file location. There is also an additional, optional, part of Haxchi called "Coldboot Haxchi" or CBHC. CBHC allows custom firmware to be enabled automatically each time the system is turned on by running the Virtual Console game directly on boot, whereas other exploits have to be run every time manually. However, CBHC has an increased risk of rendering the system inoperable as deleting the Virtual Console game, among other things, will brick the console.[74]
Many homebrew applications that run via the Homebrew Launcher have been collected and hosted on wiiubru.com, which has a layout similar to that of the Wii U's own menu. These hosted applications can be downloaded directly on the Wii U using The Homebrew App Store app in the repository. Some of these applications utilize an IOSU exploit that was released by the WiiUbru team, which allows full access to any Wii U console.[75] This IOSU exploit is often used to launch a console into a patched mode called CFW (custom firmware) sysNAND. In this patched mode, the system is able to launch any title, including unofficial titles and titles without valid signatures and virtual Wii games or injections that are shortcuts to vWii (Wii Mode) games or homebrew applications. All of the current CFWs allow editing of files stored on the Wii U via an internet connection and an FTP application as well.
The Wii U's built-in emulated Wii environment (often nicknamed vWii or Wii Mode) is capable of running Wii homebrew, such as The Homebrew Channel.[76] However, vWii is much more fragile than a real Wii console and has a higher chance of being rendered inoperable if dangerous software is used. Also, due to changes made to the Wii operating system in vWii mode, previous exploits that utilized the Wii Menu itself to load the HackMii Installer, such as Letterbomb, do not work on vWii. However, exploits that launch the HackMii Installer via a game still work on vWii. The only way to hack vWii without one of the exploit games is by using an application called wuphax. Wuphax uses the public Wii U IOSU exploit to temporarily inject the HackMii installer into the Mii Channel so that The Homebrew Channel can be installed without an exploit game.[77]
Switch[]
This section is written like a manual or guidebook. (March 2018) |
The Nintendo Switch got its first exploit with PegaSwitch on March 14, 2017; just 11 days after the console's release. It was developed by a team called ReSwitched, and it can be run through the browser included when connecting to a Wi-Fi network with a login page. Luca Todesco used the same exploit to jailbreak iOS 9 devices in 2016. It did not allow true homebrew to run on the system at the time, but it let developers look for other security bugs in the system. On October 1, 2017, ReSwitched announced many new exploits and tools allowing developers to start working on homebrew programs for the system even before they could be launched.[78] At the 34c3 event, hackers Plutoo, Derrek, and Naehrwert announced a kernel exploit for the system (which they said would not be released) and said that a homebrew launcher was coming soon.[79] On January 7, 2018, fail0verflow posted a video to Twitter showing a simple side-scrolling text program before booting the system, which shows that there is a way to run code before boot, opening up possibilities for new programs focused on development.[80] A homebrew launcher application has been released as well,[81] and a custom firmware called Atmosphere, has also been released.[82] Access to a Japanese copy of Puyo Puyo Tetris is initially required to install a Fake News exploit to launch the CFW on 1.0.0. For later system versions, the ability to install depends on the age of the console, as new consoles first appearing in June 2018 and shipping with system version 4.1.0 have their bootroms patched against the TrustZone (full control) exploit that allows CFW to be installed. As long as the system does not have the patches (which can only be installed at the factory during console assembly), the exploit can be used to install CFW.[83]
On March 29, 2018, SciresM, a respected developer in the homebrew community, announced that custom firmware called "Atmosphere" would be released for all available firmware versions at the time.[84] Firmware above 1.0.0 are hackable via a cold boot exploit known as Fusée Gelée developed by the Reswitched team. This exploit takes advantage of a bug in the boot ROM on the Tegra X1 chip used by the Nintendo Switch. The exploit was also independently discovered by Fail0verflow under the name ShofEL2. Firmware version 1.0.0 will be hackable via a Trustzone exploit known as Jamais Vu. Atmosphere released its first public build in October 2018, which supports all system versions.
Xbox One[]
This section needs expansion. You can help by . (July 2018) |
The Xbox One has a Dev Mode which, though intended to be used for retail game development, can be used to run unsigned homebrew software.[85] It can be enabled on any retail Xbox One console. Dev Mode disables retail games and software while enabled. Homebrew software can be developed as Universal Windows Platform applications, allowing many programs designed to run on desktop editions of Windows 10 to run on the console including console emulators. In order to activate developer mode, one has first register for an app developer account, which has a fee of $19.[86]
See also[]
- Fangame
- Mod (video gaming)
- ROM hacking
- Jailbreaking
- Modchips
References[]
- ^ Winterhalter, Ryan (April 29, 2011). "31 Homebrew Games Worth Playing". 1UP.com. Retrieved December 12, 2013.
- ^ "Odball for Magnavox Odyssey Official Page". Revrob.com. 2010-08-04. Retrieved 2012-04-03.
- ^ "Dodgeball – Magnavox Osyssey". Atari2600Land.com. 2012-07-17. Retrieved 2012-07-17.
- ^ "Sean Riddle's Home Page – Channel F info". Seanriddle.com. 2004-06-16. Retrieved 2012-04-03.
- ^ "PowerPak – RetroZone". Retrousb.com. Retrieved 2012-04-03.
- ^ "This Guy Is Making an All-New Sega Genesis Game the 90s Way". Motherboard. 14 November 2016.
- ^ https://m.youtube.com/watch?v=iJNazRuMeLc
- ^ NGDevTeam.com
- ^ Razoola (23 January 2015). "Neo Geo Dev: Two Player Skeleton game driver". Retrieved 11 February 2018 – via YouTube.
- ^ "History on what's new on the Jaguar Server Home Page?". Jaguar Server Homepage. Retrieved 2018-04-07.
- ^ Johnston, Chris (April 8, 2000). "Atari Goes to Hasbro". GameSpot.
- ^ "The Atari Jaguar 64-Bit Multimedia Entertainment System". Atari Explorer. Retrieved 2018-04-07.
- ^ "Hasbro Releases Jaguar Publishing Rights". Hasbro Interactive. Retrieved 2018-04-07.
Beverly, MA (May 14, 1999) – Leading entertainment software publisher, Hasbro Interactive announced today it has released all rights that it may have to the vintage Atari hardware platform, the Jaguar.
- ^ Goss, Patrick. "Redundant gadgets (Atari Jaguar entry)". Archived from the original on October 11, 2007. Retrieved 2018-04-07.
- ^ "THE SEMIOFFICIAL BATTLESPHERE FAQ". Official BattleSphere Home Page. Retrieved 2018-04-07.
- ^ "B & C Computervisions myatari.com atarijag.txt". B&C Computervisions. Retrieved 2018-04-07.
- ^ "Reboot - Releases". Reboot. Retrieved 2018-04-07.
- ^ "Jaguar File-Store". Atari Museum. Retrieved 2018-04-07.
- ^ "Atari Jaguar CD Encryption Bypass BIOS Kit". Consoles5.com. Retrieved 2018-04-07.
- ^ Charnock, Tom (April 17, 2015). "Fantasy World Dizzy, Rick Dangerous & Other Atari ST Classics Ported To Atari Jaguar". retrocollect.com. Retrieved 2018-11-23.
- ^ Yarusso, Albert. "Jaguar Ports on Cart Available Here!". AtariAge. Archived from the original on 28 November 2016. Retrieved 2018-04-07.
- ^ Gaztee (February 1, 2017). "ST Port Boxsets Pre-Order Now OPEN". AtariAge. Retrieved 2018-11-23.
- ^ https://mag.mo5.com/actu/98808/16-portages-de-jeux-st-sur-jaguar-en-cartouche/
- ^ CyranoJ (December 11, 2015). "Atari ST Games Ported to the Jaguar". AtariAge. Retrieved 2018-11-23.
- ^ "Jo Sega Saturn Engine, Sega Saturn SDK for homebrews". jo-engine.org. Retrieved 2017-10-18.
- ^ XL2 (2018-08-30), (Sega Saturn homebrew) Sonic Z-Treme 2018-08-30, retrieved 2018-08-30
- ^ KR155E. "Planet Virtual Boy". www.planetvb.com. Retrieved 11 February 2018.
- ^ "Archived copy". Archived from the original on 2013-03-28. Retrieved 2012-08-24.CS1 maint: archived copy as title (link)
- ^ EverDrive 64 Archived 2013-01-05 at the Wayback Machine
- ^ "64drive by Retroactive".
- ^ Agnello, Anthony John (November 19, 2013). "Back from the dead: 9 modern games for obsolete consoles". The A.V. Club. Retrieved December 12, 2013.
- ^ Brightman, James (June 20, 2006). "U.K. Court: PS2 Not a Computer". GameDaily. Archived from the original on May 4, 2010.
- ^ Simple Media System for PlayStation 2 – http://home.casema.nl/eugene_plotnikov/
- ^ FMCB 1.9 series release thread - http://psx-scene.com/forums/f153/fmcb-v1-9-series-release-thread-116247/
- ^ PS2 Emulators – http://www.sksapps.com/index.php?page=emus.html Archived 2008-06-12 at the Wayback Machine
- ^ "Booting Homebrew".
- ^ emukidid (2019-05-27), GitHub - emukidid/swiss-gc: Swiss: The swiss army knife of GameCube homebrew., retrieved 2019-05-27
- ^ "Game Boy Interface - GC-Forever Wiki". www.gc-forever.com. Retrieved 2019-05-27.
- ^ "List of DS homebrew emulators - GameBrew - a wiki dedicated to Video Game Homebrew". gamebrew.org. Retrieved 2021-05-29.
- ^ "What Are Nintendo DS and DSi Cards?". Nintendo DS Cards. June 27, 2010. Archived from the original on February 3, 2011. Retrieved September 23, 2010.
- ^ "ニンテンドーDSの違法コピーにご注意!" (in Japanese). The Chosun Ilbo. December 11, 2007. Archived from the original on February 7, 2010. Retrieved September 10, 2008.
- ^ "DSi Action Replay - Codejunkies US". web.archive.org. 2012-11-14. Retrieved 2021-05-29.
- ^ "Homebrew DS-DSLR Uses Nintendo DS as a Canon EOS Remote". Retrieved 2019-10-05.
- ^ "Memory Pit Exploit for DSi - All DSi Can Now Be Hacked via The Camera". TheNerdMag. 2019-05-28. Retrieved 2021-05-29.
- ^ "Sony blocks OtherOS in firmware 3.21". Retrieved 2012-04-14.
- ^ "Sixaxis driver for Windows XP". Archived from the original on 2007-09-01.
- ^ "How to run a PS3 game backup".
- ^ "PlayStation 3 Service Mode JIG Set-Up Files Leaked!".
- ^ "Open Source PS JailBreak Clone "PSGroove" Available Now! | PS3-Hacks :: Hack your PlayStation 3". PS3-Hacks. Retrieved 2012-04-03.
- ^ "Web hosting, domain name registration and web services by 1&1 Internet". Howtohackps3.com. Archived from the original on 2012-04-02. Retrieved 2012-04-03.
- ^ "Geohotz Page".
- ^ Sony follows up, officially sues Geohot and fail0verflow over PS3 jailbreak. Nilay Patel, Engadget (2011-01-12). Retrieved on 2011-02-16.
- ^ "For your enjoyment: WiiCade".
- ^ Wilson, Mark. "Nintendo Wii Hacked, The Video".
- ^ "Wii Homebrew Channel turns 1.0".
- ^ "New free homebrew entry point. FlashHax". GBAtemp.net - The Independent Video Game Community. Retrieved 2018-06-14.
- ^ "LetterBomb". please.hackmii.com. Retrieved 2017-06-30.
- ^ "Revolutionary: Web Wii Wares".
- ^ Brophy-Warren, Jamin (29 April 2007). "Magic Wand: How Hackers Make Use Of Their Wii-motes" – via Wall Street Journal.
- ^ Gerig, Dexter (2019-11-16), An implementation of CVE-2009-0689 for the Nintendo Wii.: Fullmetal5/str2hax, retrieved 2019-12-02
- ^ Gerig, Dexter (2019-11-22), GitHub - Fullmetal5/bluebomb: A Bluetooth exploit for the Nintendo Wii., retrieved 2019-12-02
- ^ "Freakyhax Website".
- ^ "Doodlebomb".
- ^ "yellows8/3ds_smashbroshax".
- ^ "IsTitleAllowed Documentation".
- ^ "11.6.0-39 Documentation".
- ^ "Notehax".
- ^ Homebrew, Nintendo. "Seedminer". 3DS Hacks Guide. Retrieved 2020-12-16.
- ^ "HENkaku". henkaku.xyz. Retrieved 2018-10-16.
- ^ "Modoru". GitHub. Retrieved 2019-06-24.
- ^ "Build system and examples for running C code on the Wii U". 4 March 2015. Retrieved 20 February 2015.
- ^ "Wii U libstagefright exploits". 13 January 2016. Retrieved 20 February 2016.
- ^ "Wii U Hacking & Homebrew Discussion". 13 January 2016. Retrieved 20 February 2016.
- ^ "Wii U Hacks Guide". wiiu.hacks.guide. Retrieved 2020-12-26.
- ^ "Wiiubru on GBATemp". 22 October 2016. Retrieved 17 November 2016.
- ^ "WiiMode". 3 February 2016. Retrieved 20 February 2016.
- ^ "Official - wuphax v1.1 - Hacking vWii from WiiU Mode". Retrieved 11 February 2018.
- ^ "octrelease". 1 October 2017. Retrieved 4 February 2018.
- ^ "Nintendo Switch Kernel exploit 34c3 presentation: "Nvidia Backdoored themselves"". 29 December 2017. Retrieved 4 February 2018.
- ^ @fail0verflow (7 January 2018). "We made a nice scroller for Switch :)" (Tweet). Retrieved 4 February 2018 – via Twitter.
- ^ https://switchbrew.github.io/nx-hbl/
- ^ @SciresM (3 March 2018). "Exosphere (A TrustZone re-implementation in Atmosphere, my Switch CFW) just successfully performed smcCpuOn, turnin…" (Tweet) – via Twitter.
- ^ https://reinx.guide/firsttime
- ^ "An update on timelines • r/SwitchHacks". reddit. Retrieved 2018-03-29.
- ^ "Developer Mode Activation App FAQ". support.xbox.com. Retrieved 2018-07-04.
- ^ "Register as an app developer". developer.microsoft.com. Retrieved 2021-05-16.
External links[]
- Custom firmware
- Homebrew software
- Video game development
- Dedicated consoles