SIM card


A SIM card, also known as subscriber identity module or subscriber identification module (SIM), is an integrated circuit running a card operating system (COS) that is intended to securely store the international mobile subscriber identity (IMSI) number and its related key, which are used to identify and authenticate subscribers on mobile telephony devices (such as mobile phones and computers). It is also possible to store contact information on many SIM cards. SIM cards are always used on GSM phones; for CDMA phones, they are needed only for LTE-capable handsets. SIM cards can also be used in satellite phones, smart watches, computers, or cameras.
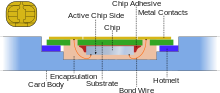
The SIM circuit is part of the function of a universal integrated circuit card (UICC) physical smart card, which is usually made of PVC with embedded contacts and semiconductors. SIM cards are transferable between different mobile devices. The first UICC smart cards were the size of credit and bank cards; sizes were reduced several times over the years, usually keeping electrical contacts the same, so that a larger card could be cut down to a smaller size.
A SIM card contains a unique serial number (ICCID), international mobile subscriber identity (IMSI) number, security authentication and ciphering information, temporary information related to the local network, a list of the services the user has access to, and two passwords: a personal identification number (PIN) for ordinary use, and a personal unblocking key (PUK) for PIN unlocking. In Europe, the serial SIM number (SSN) is also sometimes accompanied by an international article number (IAN) or a European article number (EAN) required when registering online for the subscription of a prepaid card.
History and procurement[]
The SIM card is a type of smart card,[1] the basis for which is the silicon integrated circuit (IC) chip.[2] The idea of incorporating a silicon IC chip onto a plastic card originates from the late 1960s.[2] Smart cards have since used MOS integrated circuit chips, along with MOS memory technologies such as flash memory and EEPROM (electrically erasable programmable read-only memory).[3]
The SIM was initially specified by the European Telecommunications Standards Institute in the specification with the number TS 11.11. This specification describes the physical and logical behaviour of the SIM. With the development of UMTS, the specification work was partially transferred to 3GPP. 3GPP is now responsible for the further development of applications like SIM (TS 51.011[4]) and USIM (TS 31.102[5]) and ETSI for the further development of the physical card UICC.
The first SIM card was developed in 1991 by Munich smart-card maker Giesecke & Devrient, who sold the first 300 SIM cards to the Finnish wireless network operator Radiolinja.[6][7]
Today, SIM cards are ubiquitous, allowing over 7 billion devices to connect to cellular networks around the world. According to the International Card Manufacturers Association (ICMA), there were 5.4 billion SIM cards manufactured globally in 2016 creating over $6.5 billion in revenue for traditional SIM card vendors.[8] The rise of cellular IoT and 5G networks is predicted to drive the growth of the addressable market for SIM card manufacturers to over 20 billion cellular devices by 2020.[9] The introduction of embedded-SIM (eSIM) and remote SIM provisioning (RSP) from the GSMA[10] may[clarification needed] disrupt the traditional SIM card ecosystem with the entrance of new players specializing in "digital" SIM card provisioning and other value-added services for mobile network operators.
Design[]
There are three operating voltages for SIM cards: 5 V, 3 V and 1.8 V (ISO/IEC 7816-3 classes A, B and C, respectively). The operating voltage of the majority of SIM cards launched before 1998 was 5 V. SIM cards produced subsequently are compatible with 3 V and 5 V. Modern cards support 5 V, 3 V and 1.8 V[citation needed].

Modern SIM cards allow applications to load when the SIM is in use by the subscriber. These applications communicate with the handset or a server using SIM Application Toolkit, which was initially specified by 3GPP in TS 11.14. (There is an identical ETSI specification with different numbering.) ETSI and 3GPP maintain the SIM specifications. The main specifications are: ETSI TS 102 223 (the toolkit for smartcards), ETSI TS 102 241 (API), ETSI TS 102 588 (application invocation), and ETSI TS 131 111 (toolkit for more SIM-likes). SIM toolkit applications were initially written in native code using proprietary APIs. To provide interoperability of the applications, ETSI chose Java Card.[11] A multi-company collaboration called GlobalPlatform defines some extensions on the cards, with additional APIs and features like more cryptographic security and RFID contactless use added.[12]
Data[]
SIM cards store network-specific information used to authenticate and identify subscribers on the network. The most important of these are the ICCID, IMSI, authentication key (Ki), local area identity (LAI) and operator-specific emergency number. The SIM also stores other carrier-specific data such as the SMSC (Short Message service center) number, service provider name (SPN), service dialling numbers (SDN), advice-of-charge parameters and value-added service (VAS) applications. (Refer to GSM 11.11.[13])
SIM cards can come in various data capacities, from 8 KB to at least 256 KB.[citation needed] All can store a maximum of 250 contacts on the SIM, but while the 32 KB has room for 33 mobile network codes (MNCs) or network identifiers, the 64 KB version has room for 80 MNCs.[citation needed] This is used by network operators to store data on preferred networks, mostly used when the SIM is not in its home network but is roaming. The network operator that issued the SIM card can use this to have a phone connect to a preferred network that is more economic for the provider instead of having to pay the network operator that the phone discovered first. This does not mean that a phone containing this SIM card can connect to a maximum of only 33 or 80 networks, but it means that the SIM card issuer can specify only up to that number of preferred networks. If a SIM is outside these preferred networks it uses the first or best available network.[citation needed]
ICCID[]
Each SIM is internationally identified by its integrated circuit card identifier (ICCID). ICCID is the identifier of the actual SIM card itself – i.e. an identifier for the SIM chip. Nowadays ICCID numbers are also used to identify eSIM profiles, and not only physical SIM cards. ICCIDs are stored in the SIM cards and are also engraved or printed on the SIM card body during a process called personalisation. The ICCID is defined by the ITU-T recommendation E.118 as the primary account number.[14] Its layout is based on ISO/IEC 7812. According to E.118, the number can be up to 22 digits long, including a single check digit calculated using the Luhn algorithm. However, the GSM Phase 1[15] defined the ICCID length as an opaque data field, 10 octets (20 digits) in length, whose structure is specific to a mobile network operator.
The number is composed of the following subparts:
Issuer identification number (IIN)
Maximum of seven digits:
- Major industry identifier (MII), 2 fixed digits, 89 for telecommunication purposes.
- Country code, 2 or 3 digits, as defined by ITU-T recommendation E.164.
- NANP countries, apart from Canada, use 01, i.e. prepending a zero to their common calling code +1
- Canada uses 302
- Russia uses 701, i.e. appending 01 to its calling code +7
- Kazakhstan uses 997, even though it shares the calling code +7 with Russia
- Issuer identifier, 1–4 digits.
- Often identical to the mobile network code (MNC).[citation needed]
Individual account identification
- Individual account identification number. Its length is variable, but every number under one IIN has the same length.
- Often identical to the mobile subscription identification number (MSIN).[citation needed]
Check digit
- Single digit calculated from the other digits using the Luhn algorithm.
With the GSM Phase 1 specification using 10 octets into which ICCID is stored as packed BCD, the data field has room for 20 digits with hexadecimal digit "F" being used as filler when necessary.
In practice, this means that on GSM SIM cards there are 20-digit (19+1) and 19-digit (18+1) ICCIDs in use, depending upon the issuer. However, a single issuer always uses the same size for its ICCIDs.
To confuse matters more, SIM factories seem to have varying ways of delivering electronic copies of SIM personalization datasets. Some datasets are without the ICCID checksum digit, others are with the digit.
As required by E.118, the ITU-T updates a list of all current internationally assigned IIN codes in its Operational Bulletins which are published twice a month (the last as of January 2019 was No. 1163 from 1 January 2019).[16] ITU-T also publishes complete lists: as of January 2019, the list issued on 1 December 2018 was current, having all issuer identifier numbers before 1 December 2018.[17]
International mobile subscriber identity (IMSI)[]
SIM cards are identified on their individual operator networks by a unique international mobile subscriber identity (IMSI). Mobile network operators connect mobile phone calls and communicate with their market SIM cards using their IMSIs. The format is:
- The first three digits represent the mobile country code (MCC).
- The next two or three digits represent the mobile network code (MNC). Three-digit MNC codes are allowed by E.212 but are mainly used in the United States and Canada. One MCC can have both 2 digit and 3 digit MNCs, an example is 350 007.
- The next digits represent the mobile subscriber identification number (MSIN). Normally there are 10 digits, but can be fewer in the case of a 3-digit MNC or if national regulations indicate that the total length of the IMSI should be less than 15 digits.
- Digits are different from country to country.
Authentication key (Ki)[]
The Ki is a 128-bit value used in authenticating the SIMs on a GSM mobile network (for USIM network, you still need Ki but other parameters are also needed). Each SIM holds a unique Ki assigned to it by the operator during the personalization process. The Ki is also stored in a database (termed authentication center or AuC) on the carrier's network.
The SIM card is designed to prevent someone from getting the Ki by using the smart-card interface. Instead, the SIM card provides a function, Run GSM Algorithm, that the phone uses to pass data to the SIM card to be signed with the Ki. This, by design, makes using the SIM card mandatory unless the Ki can be extracted from the SIM card, or the carrier is willing to reveal the Ki. In practice, the GSM cryptographic algorithm for computing a signed response (SRES_1/SRES_2: see steps 3 and 4, below) from the Ki has certain vulnerabilities[18] that can allow the extraction of the Ki from a SIM card and the making of a duplicate SIM card.
Authentication process:
- When the mobile equipment starts up, it obtains the international mobile subscriber identity (IMSI) from the SIM card, and passes this to the mobile operator, requesting access and authentication. The mobile equipment may have to pass a PIN to the SIM card before the SIM card reveals this information.
- The operator network searches its database for the incoming IMSI and its associated Ki.
- The operator network then generates a random number (RAND, which is a nonce) and signs it with the Ki associated with the IMSI (and stored on the SIM card), computing another number, that is split into the Signed Response 1 (SRES_1, 32 bits) and the encryption key Kc (64 bits).
- The operator network then sends the RAND to the mobile equipment, which passes it to the SIM card. The SIM card signs it with its Ki, producing Signed Response 2 (SRES_2) and Kc, which it gives to the mobile equipment. The mobile equipment passes SRES_2 on to the operator network.
- The operator network then compares its computed SRES_1 with the computed SRES_2 that the mobile equipment returned. If the two numbers match, the SIM is authenticated and the mobile equipment is granted access to the operator's network. Kc is used to encrypt all further communications between the mobile equipment and the operator.
Location area identity[]
The SIM stores network state information, which is received from the location area identity (LAI). Operator networks are divided into location areas, each having a unique LAI number. When the device changes locations, it stores the new LAI to the SIM and sends it back to the operator network with its new location. If the device is power cycled, it takes data off the SIM, and searches for the prior LAI.
SMS messages and contacts[]
Most SIM cards store a number of SMS messages and phone book contacts. It stores the contacts in simple "name and number" pairs. Entries that contain multiple phone numbers and additional phone numbers are usually not stored on the SIM card. When a user tries to copy such entries to a SIM, the handset's software breaks them into multiple entries, discarding information that is not a phone number. The number of contacts and messages stored depends on the SIM; early models stored as few as five messages and 20 contacts, while modern SIM cards can usually store over 250 contacts.[citation needed]
Formats[]
SIM cards have been made smaller over the years; functionality is independent of format. Full-size SIM was followed by mini-SIM, micro-SIM, and nano-SIM. SIM cards are also made to embed in devices.

| SIM card format | Introduced | Standard reference | Length | Width | Thickness |
|---|---|---|---|---|---|
| Full-size (1FF) | 1991 | ISO/IEC 7810:2003, ID-1 | 85.6 mm (3.37 in) | 53.98 mm (2.125 in) | 0.76 mm (0.030 in) |
| Mini-SIM (2FF) | 1996 | ISO/IEC 7810:2003, ID-000 | 25 mm (0.98 in) | 15 mm (0.59 in) | 0.76 mm (0.030 in) |
| Micro-SIM (3FF) | 2003 | ETSI TS 102 221 V9.0.0, Mini-UICC | 15 mm (0.59 in) | 12 mm (0.47 in) | 0.76 mm (0.030 in) |
| Nano-SIM (4FF) | early 2012 | ETSI TS 102 221 V11.0.0 | 12.3 mm (0.48 in) | 8.8 mm (0.35 in) | 0.67 mm (0.026 in) |
| Embedded-SIM (eSIM) |
2016 | ETSI TS 102.671 V9.0.0
JEDEC Design Guide 4.8, SON-8 |
— | — | — |
All versions of the non-embedded SIM cards share the same ISO/IEC 7816 pin arrangement.
Full-size SIM[]
The full-size SIM (or 1FF, 1st form factor) was the first form factor to appear. It was the size of a credit card (85.60 mm × 53.98 mm × 0.76 mm). Later smaller SIMs are often supplied embedded in a full-size card from which they can be removed.
Mini-SIM[]


The mini-SIM (or 2FF) card has the same contact arrangement as the full-size SIM card and is normally supplied within a full-size card carrier, attached by a number of linking pieces. This arrangement (defined in ISO/IEC 7810 as ID-1/000) lets such a card be used in a device that requires a full-size card – or in a device that requires a mini-SIM card, after breaking the linking pieces. As the full-size SIM is no longer used, some suppliers refer to the mini-SIM as a "standard SIM" or "regular SIM".
Micro-SIM[]
The micro-SIM (or 3FF) card has the same thickness and contact arrangements, but reduced length and width as shown in the table above.[19]
The micro-SIM was introduced by the European Telecommunications Standards Institute (ETSI) along with SCP, 3GPP (UTRAN/GERAN), 3GPP2 (CDMA2000), ARIB, GSM Association (GSMA SCaG and GSMNA), GlobalPlatform, Liberty Alliance, and the Open Mobile Alliance (OMA) for the purpose of fitting into devices too small for a mini-SIM card.[20][21]
The form factor was mentioned in the December 1998 3GPP SMG9 UMTS Working Party, which is the standards-setting body for GSM SIM cards,[22] and the form factor was agreed upon in late 2003.[23]
The micro-SIM was designed for backward compatibility. The major issue for backward compatibility was the contact area of the chip. Retaining the same contact area makes the micro-SIM compatible with the prior, larger SIM readers through the use of plastic cutout surrounds. The SIM was also designed to run at the same speed (5 MHz) as the prior version. The same size and positions of pins resulted in numerous "How-to" tutorials and YouTube videos with detailed instructions how to cut a mini-SIM card to micro-SIM size.[24]
The chairman of EP SCP, Dr Klaus Vedder, said[23]
ETSI has responded to a market need from ETSI customers, but additionally there is a strong desire not to invalidate, overnight, the existing interface, nor reduce the performance of the cards.
Micro-SIM cards were introduced by various mobile service providers for the launch of the original iPad, and later for smartphones, from April 2010. The iPhone 4 was the first smartphone to use a micro-SIM card in June 2010, followed by many others.
Nano-SIM[]
The nano-SIM (or 4FF) card was introduced on 11 October 2012, when mobile service providers in various countries started to supply it for phones that supported the format. The nano-SIM measures 12.3 mm × 8.8 mm × 0.67 mm (0.484 in × 0.346 in × 0.026 in) and reduces the previous format to the contact area while maintaining the existing contact arrangements. A small rim of isolating material is left around the contact area to avoid short circuits with the socket. The nano-SIM is 0.67 mm (0.026 in) thick, compared to the 0.76 mm (0.030 in) of its predecessors. 4FF can be put into adapters for use with devices designed for 2FF or 3FF SIMs, and is made thinner for that purpose,[25] and telephone companies give due warning about this.[26]
The iPhone 5, released in September 2012, was the first device to use a nano-SIM card, followed by other handsets.
Security[]
In July 2013, Karsten Nohl, a security researcher from SRLabs, described[27][28] vulnerabilities in some SIM cards that supported DES, which, despite its age, is still used by some operators.[28] The attack could lead to the phone being remotely cloned or let someone steal payment credentials from the SIM.[28] Further details of the research were provided at BlackHat on 31 July 2013.[28][29]
In response, the International Telecommunication Union said that the development was "hugely significant" and that it would be contacting its members.[30]
In February 2015, it was reported by The Intercept that the NSA and GCHQ had stolen the encryption keys (Ki's) used by Gemalto (the manufacturer of 2 billion SIM cards annually), enabling these intelligence agencies to monitor voice and data communications without the knowledge or approval of cellular network providers or judicial oversight.[31] Having finished its investigation, Gemalto claimed that it has “reasonable grounds” to believe that the NSA and GCHQ carried out an operation to hack its network in 2010 and 2011, but says the number of possibly stolen keys would not have been massive.[32]
In September 2019, Cathal Mc Daid, a security researcher from AdaptiveMobile Security, described[33][34] how vulnerabilities in some SIM cards that contained the S@T Browser library were being actively exploited. This vulnerability was named Simjacker. Attackers were using the vulnerability to track the location of thousands of mobile phone users in several countries.[35] Further details of the research were provided at VirusBulletin on 3 October 2019.[36][37]
Developments[]
When GSM was already in use, the specifications were further developed and enhanced with functionality such as SMS and GPRS. These development steps are referred as releases by ETSI. Within these development cycles, the SIM specification was enhanced as well: new voltage classes, formats and files were introduced.
USIM[]
In GSM-only times, the SIM consisted of the hardware and the software. With the advent of UMTS, this naming was split: the SIM was now an application and hence only software. The hardware part was called UICC. This split was necessary because UMTS introduced a new application, the universal subscriber identity module (USIM). The USIM brought, among other things, security improvements like mutual authentication and longer encryption keys and an improved address book.
UICC[]
"SIM cards" in developed countries today are usually UICCs containing at least a SIM application and a USIM application. This configuration is necessary because older GSM only handsets are solely compatible with the SIM application and some UMTS security enhancements rely on the USIM application.
Other variants[]
On cdmaOne networks, the equivalent of the SIM card is the R-UIM and the equivalent of the SIM application is the CSIM.
A virtual SIM is a mobile phone number provided by a mobile network operator that does not require a SIM card to connect phone calls to a user's mobile phone.
Embedded-SIM (eSIM)[]

An embedded SIM (eSIM) is a form of programmable SIM that is embedded directly into a device. The surface mount format provides the same electrical interface as the full size, 2FF and 3FF SIM cards, but is soldered to a circuit board as part of the manufacturing process. In M2M applications where there is no requirement[10] to change the SIM card, this avoids the requirement for a connector, improving reliability and security. An eSIM can be provisioned remotely; end-users can add or remove operators without the need to physically swap a SIM from the device.[38]
Usage in mobile phone standards[]

The use of SIM cards is mandatory in GSM devices.
The satellite phone networks Iridium, Thuraya and Inmarsat's BGAN also use SIM cards. Sometimes, these SIM cards work in regular GSM phones and also allow GSM customers to roam in satellite networks by using their own SIM cards in a satellite phone.
Japan's 2G PDC system (which was shut down in 2012; SoftBank Mobile has already shut down PDC from 31 March 2010) also specifies a SIM, but this has never been implemented commercially. The specification of the interface between the Mobile Equipment and the SIM is given in the RCR STD-27 annexe 4. The Subscriber Identity Module Expert Group was a committee of specialists assembled by the European Telecommunications Standards Institute (ETSI) to draw up the specifications (GSM 11.11) for interfacing between smart cards and mobile telephones. In 1994, the name SIMEG was changed to SMG9.
Japan's current and next-generation cellular systems are based on W-CDMA (UMTS) and CDMA2000 and all use SIM cards. However, Japanese CDMA2000-based phones are locked to the R-UIM they are associated with and thus, the cards are not interchangeable with other Japanese CDMA2000 handsets (though they may be inserted into GSM/WCDMA handsets for roaming purposes outside Japan).
CDMA-based devices originally did not use a removable card, and the service for these phones is bound to a unique identifier contained in the handset itself. This is most prevalent in operators in the Americas. The first publication of the TIA-820 standard (also known as 3GPP2 C.S0023) in 2000 defined the Removable User Identity Module (R-UIM). Card-based CDMA devices are most prevalent in Asia.
The equivalent of a SIM in UMTS is called the universal integrated circuit card (UICC), which runs a USIM application. The UICC is still colloquially called a SIM card.[39]

SIM card for Thuraya satellite phone

KDDI's au IC-Card

NTT DoCoMo's FOMA card

UMTS modem with Beeline's SIM card

SIM card and the mobile phone

Three UK SIM card with packaging

H2O Wireless prepaid SIM card

Deutsche Telekom mini-SIM with pre-cut micro- and nano-SIM

A mini-SIM card next to its electrical contacts in a Nokia 6233

Nano-SIM card
SIM and carriers[]
The SIM card introduced a new and significant business opportunity for MVNOs – mobile virtual network operators – who lease capacity from one of the network operators rather than owning or operating a cellular telecoms network and only provide a SIM card to their customers. MVNOs first appeared in Denmark, Hong Kong, Finland and the UK. Today they exist in over 50 countries, including most of Europe, the United States, Canada, Mexico, Australia and parts of Asia, and account for approximately 10% of all mobile phone subscribers around the world.[citation needed]
On some networks, the mobile phone is locked to its carrier SIM card, meaning that the phone only works with SIM cards from the specific carrier. This is more common in markets where mobile phones are heavily subsidised by the carriers, and the business model depends on the customer staying with the service provider for a minimum term (typically 12, 18 or 24 months). SIM cards that are issued by providers with an associated contract are called SIM-only deals. Common examples are the GSM networks in the United States, Canada, Australia, the UK and Poland. Many businesses offer the ability to remove the SIM lock from a phone, effectively making it possible to then use the phone on any network by inserting a different SIM card. Mostly, GSM and 3G mobile handsets can easily be unlocked and used on any suitable network with any SIM card.
In countries where the phones are not subsidised, e.g., India, Israel and Belgium, all phones are unlocked. Where the phone is not locked to its SIM card, the users can easily switch networks by simply replacing the SIM card of one network with that of another while using only one phone. This is typical, for example, among users who may want to optimise their carrier's traffic by different tariffs to different friends on different networks, or when travelling internationally.
In 2016, carriers started using the concept of automatic SIM reactivation[40] whereby they let users reuse expired SIM cards instead of purchasing new ones when they wish to re-subscribe to that operator. This is particularly useful in countries where prepaid calls dominate and where competition drives high churn rates, as users had to return to a carrier shop to purchase a new SIM each time they wanted to churn back to an operator.
SIM-only[]
Commonly sold as a product by mobile telecommunications companies, "SIM-only" refers to a type of legally binding contract between a mobile network provider and a customer. The contract itself takes the form of a credit agreement and is subject to a credit check.
Within a SIM-only contract, the mobile network provider supplies their customer with just one piece of hardware, a SIM card, which includes an agreed amount of network usage in exchange for a monthly payment. Network usage within a SIM-only contract can be measured in minutes, text, data or any combination of these. The duration of a SIM-only contract varies depending on the deal selected by the customer, but in the UK they are available over 1, 3, 6, and 12-month periods.
SIM-only contracts differ from mobile phone contracts in that they do not include any hardware other than a SIM card. In terms of network usage, SIM-only is typically more cost-effective than other contracts because the provider does not charge more to offset the cost of a mobile device over the contract period. The short contract length is one of the key features of SIM-only – made possible by the absence of a mobile device.
SIM-only is increasing in popularity very quickly.[41] In 2010 pay monthly based mobile phone subscriptions grew from 41 per cent to 49 per cent of all UK mobile phone subscriptions.[42] According to German research company GfK, 250,000 SIM-only mobile contracts were taken up in the UK during July 2012 alone, the highest figure since GfK began keeping records.
Increasing smartphone penetration combined with financial concerns is leading customers to save money by moving onto a SIM-only when their initial contract term is over.
Multiple-SIM devices[]

Dual SIM devices have two SIM card slots for the use of two SIM cards, from one or multiple carriers. Multiple SIM devices are commonplace in developing markets such as in Africa, East Asia, South Asia and Southeast Asia, where variable billing rates, network coverage and speed make it desirable for consumers to use multiple SIMs from competing networks. Dual-SIM phones are also useful to separate one's personal phone number from a business phone number, without having to carry multiple devices. Some popular devices, such as the BlackBerry KeyOne have dual SIM variants, however, dual SIM devices were not common in the US or Europe due to lack of demand. This has changed with mainline products from Apple and Google featuring either two SIM slots or a combination of a physical SIM slot and an eSIM.
Thin SIM[]
A thin SIM (or overlay SIM or SIM overlay) is a very thin device shaped like a SIM card, approximately 120 microns thick. It has contacts on its front and back. It is used by sticking it on top of a regular SIM card. It provides its own functionality while passing through the functionality of the SIM card underneath. It can be used to bypass the mobile operating network and run custom applications, particularly on non-programmable cell phones.[43]
Its top surface is a connector that connects to the phone in place of the normal SIM. Its bottom surface is a connector that connects to the SIM in place of the phone. With electronics, it can modify signals in either direction, thus presenting a modified SIM to the phone, and/or presenting a modified phone to the SIM. It is a similar concept to the Game Genie, which connects between a game console and a game cartridge, creating a modified game.
In 2014, Equitel, an MVNO operated by Kenya's Equity Bank, announced its intention to begin issuing thin SIMs to customers, raising security concerns by competition, particularly concerning the safety of mobile money accounts. However, after months of security testing and legal hearings before the country's Parliamentary Committee on Energy, Information and Communications, the Communications Authority of Kenya (CAK) gave the bank the green light to roll out its thin SIM cards.[44]
See also[]
- Apple SIM
- GSM 03.48
- International Mobile Equipment Identity (IMEI)
- IP Multimedia Services Identity Module (ISIM)
- Mobile broadband
- Mobile equipment identifier (MEID)
- Mobile signature
- Regional lockout
- SIM cloning
- SIM connector
- Single Wire Protocol (SWP)
- Tethering
- Transponder
- GSM USSD codes – Unstructured Supplementary Service Data: list of standard GSM codes for network and SIM related functions
- VMAC
- W-SIM (Willcom-SIM)
References[]
- ^ Tait, Don (25 August 2016). "Smart card IC shipments to reach 12.8 billion units in 2021". IHS Technology. IHS Markit. Retrieved 24 October 2019.
- ^ Jump up to: a b Chen, Zhiqun (2000). Java Card Technology for Smart Cards: Architecture and Programmer's Guide. Addison-Wesley Professional. pp. 3–4. ISBN 9780201703290.
- ^ Veendrick, Harry J. M. (2017). Nanometer CMOS ICs: From Basics to ASICs. Springer. pp. 315, 481–2. ISBN 9783319475974.
- ^ "3GPP specification: 51.011". Retrieved 29 April 2016.
- ^ "3GPP specification: 31.102". Retrieved 29 April 2016.
- ^ Asif, Saad Z. (2011). Next Generation Mobile Communications Ecosystem. John Wiley & Sons. p. 306. ISBN 978-1119995814.
- ^ "G&D – History of Giesecke & Devrient". Retrieved 29 April 2016.
- ^ "Official Publication of the International Card Manufacturers Association February 2017 Volume 27 No1" (PDF). Retrieved 28 May 2017.
- ^ "Ericsson Mobility Report November 2015" (PDF). Retrieved 28 May 2017.
- ^ Jump up to: a b "GSMA Embedded SIM and RSP". Retrieved 28 May 2017.
- ^ "ETSI TS 102 241: UICC API for Java Card™ Release 13" (PDF). Retrieved 8 August 2019.
- ^ "Specifications Archive: Secure Element (Card)". GlobalPlatform.
- ^ "3GPP specification: 11.11". Retrieved 29 April 2016.
- ^ ITU-T, ITU-T Recommendation E.118, The international telecommunication charge card, Revision history, Revision "05/2006"
- ^ ETSI, ETSI Recommendation GSM 11.11, Specifications of the SIM-ME Interface, Version 3.16.0
- ^ "Operational Bulletin No. 1163 (1.I.2019)". www.itu.int. Retrieved 5 January 2019.
- ^ "List of issuer identifier numbers for the international telecommunication charge card (in accordance with Recommendation ITU-T E.118 (05/2006))". International Telecommunication Union. 5 January 2015.
- ^ "Hackers crack open mobile network". bbc.co.uk. 20 April 2011. Retrieved 13 August 2011.
- ^ "What is a microsim card?". SimOnlyPro.nl. Archived from the original on 22 February 2013. Retrieved 14 October 2012.
- ^ Gaby Lenhart (1 April 2006). "The Smart Card Platform". ETSI Technical Committee Smart Card Platform (TB SCP). Retrieved 30 January 2010.
SCP is co-operating on both technical and service aspects with a number of other committees both within and outside the telecommunications sector.
- ^ Segan, Sascha (27 January 2010). "Inside the iPad Lurks the 'Micro SIM'". PC Magazine. Retrieved 30 January 2010.
- ^ "DRAFT Report of the SMG9 UMTS Working Party, meeting #7 hosted by Nokia in Copenhagen, 15–16 December 1998" (PDF). 3GPP. 25 January 1999. Retrieved 27 January 2010.
One manufacturer stated that it may be difficult to meeting ISO mechanical standards for a combined ID-1/micro-SIM card.
- ^ Jump up to: a b Antipolis, Sophia (8 December 2003). "New form factor for smart cards introduced". SmartCard Trends. Archived from the original on 26 April 2010. Retrieved 30 January 2010.
The work item for the so-called Third Form Factor, "3FF", was agreed, after intensive discussions, at the SCP meeting held last week in London.
- ^ How to make MicroSIM on YouTube
- ^ Dr. Klaus Vedder (18 January 2012). "The UICC – Recent Work of ETSI TC Smart Card Platform" (PDF). ETSI. p. 12. Archived from the original (PDF) on 30 August 2017. Retrieved 22 July 2012.
Thinner to allow adapters so that the 4FF can be "clicked" into adapters for use as a Plug-in SIM or 3FF SIM giving a kind of backward usability
- ^ Virgin Mobile. "An important guide to inserting your SIM into your mobile" (PDF). Archived from the original (PDF) on 25 January 2018. Retrieved 21 January 2017.
You may also have to use one of the enclosed adaptors. If you don't follow these guidelines your phone warranty could be invalidated. We're afraid we can't accept responsibility for any damage to your phone if you choose to ignore this advice.
- ^ Encryption Bug in SIM Card Can be Used to Hack Millions of Phones, published 2013-07-21, accessed 2013-07-22
- ^ Jump up to: a b c d Rooting SIM cards, SR Labs, accessed 2013-07-22
- ^ "Black Hat USA 2013". Retrieved 29 April 2016.
- ^ UPDATE 1-UN warns on mobile cybersecurity bugs in bid to prevent attacks, Reuters, 2013-07-21, accessed 2013-07-21
- ^ "The Great SIM Heist – How Spies Stole the Keys to the Encryption Castle". The Intercept. The Intercept (First Look Media). 19 February 2015. Retrieved 19 February 2015.
- ^ "Gemalto: NSA/GCHQ Hack 'Probably Happened' But Didn't Include Mass SIM Key Theft". techcrunch.com. 25 February 2015. Retrieved 2 April 2015.
- ^ Cimpanu, Catalin. "Simjacker attack exploited in the wild to track users for at least two years". ZDNet. Retrieved 28 July 2021.
- ^ "Simjacker – Next Generation Spying Over Mobile | Mobile Security News | AdaptiveMobile". blog.adaptivemobile.com. Retrieved 28 July 2021.
- ^ Olson, Parmy (13 September 2019). "Hackers Use Spyware to Track SIM Cards". Wall Street Journal. ISSN 0099-9660. Retrieved 28 July 2021.
- ^ "Virus Bulletin :: Simjacker - the next frontier in mobile espionage". www.virusbulletin.com. Retrieved 28 July 2021.
- ^ "Simjacker - Frequently Asked Questions and Demos | Mobile Security News | AdaptiveMobile". blog.adaptivemobile.com. Retrieved 28 July 2021.
- ^ "eUICC – The Future for SIM Technology". PodM2M. 5 July 2019.
- ^ "Communication · Mobile Threat Catalogue". National Institute of Standards and Technology. Retrieved 19 June 2021.
…colloquially referred to as the Subscriber Identity Module (SIM) card, although current standards use the term Universal Integrated Circuit Card (UICC).
- ^ "Gemalto pioneers SIM reactivation". 3 November 2016. Retrieved 3 November 2016.
- ^ "A nation addicted to smartphones". Ofcom.
- ^ "UK sales of SIM-only mobile contracts set a new record". The Fone Cast. Retrieved 29 October 2012.
- ^ CCS 2016 (7 November 2016). "Keynote by Ross Anderson at CCS 2016" – via YouTube.
- ^ Heuler, Hilary. "Africa's new thin SIM cards: The line between banks and telcos just got thinner – ZDNet".
External links[]
| Wikimedia Commons has media related to SIM cards. |
- GSM 11.11 – Specification of the Subscriber Identity Module-Mobile Equipment (SIM-ME) interface.
- GSM 11.14 – Specification of the SIM Application Toolkit for the Subscriber Identity Module-Mobile Equipment (SIM-ME) interface
- GSM 03.48 – Specification of the security mechanisms for SIM application toolkit
- GSM 03.48 Java API – API and realization of GSM 03.48 in Java
- ITU-T E.118 – The International Telecommunication Charge Card 2006 ITU-T
- German inventions
- Mobile phone standards
- Cryptographic hardware
- Smart cards
- Computer access control









